Published on Mon, Jul 28, 2025 by Étienne Brouillard
As cloud applications evolve from simple three-tier architectures to complex microservices ecosystems, traditional networking approaches become bottlenecks to innovation. Teams struggle with VPC peering complexity, Transit Gateway costs, and the operational overhead of managing service-to-service connectivity at scale. AWS VPC Lattice emerges as a purpose-built solution that addresses these scalability, security, and operational efficiency challenges in modern cloud architectures.
VPC Lattice is a Layer 7 and Layer 4 networking service that connects, secures, and monitors microservices on AWS. When operating at the application layer, it routes HTTP/HTTPS traffic based on headers, paths, and methods—enabling intelligent service-to-service communication. When used at Layer 4, it can be used to share Amazon RDS Databases or any resource operating at the TCP level.
VPC Lattice enhances serverless applications on AWS, whether built with Lambda Functions or ECS Tasks on Fargate, by improving:
- Development: No changes to existing workflows
- Networking: Simplified connectivity between services
- Security: IAM-based access control
- Monitoring: Centralized observability
Your current AWS ECS and Lambda patterns remain valid. Development teams can maintain their CI/CD pipelines and infrastructure patterns while gaining the benefits of network decoupling.
With VPC Lattice, you no longer need to allocate enterprise IP address space for microservices. Each application can use standard VPC CIDR blocks (like 172.31.0.0/16), making VPC peering and Transit Gateway connections optional rather than required.
VPC Lattice facilitates integration with other Line of Business systems both on-premises and in AWS through AWS Resource Access Manager (RAM). Supporting both Layer 7 and Layer 4 connectivity, it simplifies complex integration scenarios by enabling both application-level and transport-level communication.
Services deployed on VPC Lattice can leverage familiar IAM policies for access control, often eliminating the need for custom authentication solutions or third-party OIDC providers.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::123456789012:role/allowed-service-role"
},
"Action": [
"vpc-lattice:Invoke"
],
"Resource": "arn:aws:vpc-lattice:us-east-1:123456789012:service/svc-*"
},
{
"Effect": "Deny",
"Principal": "*",
"Action": [
"vpc-lattice:Invoke"
],
"Resource": "arn:aws:vpc-lattice:us-east-1:123456789012:service/svc-*",
"Condition": {
"StringNotEquals": {
"aws:PrincipalArn": "arn:aws:iam::123456789012:role/allowed-service-role"
}
}
}
]
}VPC Lattice operates through a sophisticated yet straightforward mechanism:
- Service Network Creation: You create a service network that serves as the backbone for service-to-service communication.
- VPC Association: You associate one or more VPCs with this service network. A VPC can only be associated with one service network.
- Service Registration: Services (like ALBs, Lambda functions, or other AWS resources) are registered with the service network.
- Networking Magic: Behind the scenes, VPC Lattice creates special routes in your VPC routing tables that direct traffic destined for the 169.254.0.0/16 CIDR block (similar to the EC2 metadata service approach) to the Lattice infrastructure.
- DNS Resolution: VPC Lattice automatically creates DNS entries for your services, allowing applications to discover and connect to them using domain names rather than IP addresses.
This architecture eliminates the need for complex VPC peering or Transit Gateway configurations while maintaining security through IAM policies and security groups.
While VPC Lattice offers significant benefits, it's important to be aware of its service quotas and limitations:
- Service Networks: 10 per AWS Region
- Services: 500 per AWS Region
- VPC Associations: 10 per service network
- Service Associations: 500 per service network
- Listeners: 5 per service
- Rules: 5 per listener
- Target Groups: 5 per service
- Targets: 1,000 per target group
As usual, before requesting changes to limits, validate that the architecture is not the issue. Simple changes often lead to improvements that don't require quota changes.
- Request Rate: Up to 50,000 requests per second per service
- Connection Timeout: 10 seconds maximum
- Request Timeout: 60 seconds maximum
- Response Size: 1 MB maximum
- Protocol Support: HTTP/1.1, HTTP/2, gRPC, and TCP (no WebSockets or HTTP/3 yet)
- Regional Service: VPC Lattice operates within a single AWS Region
- Authentication: Only AWS IAM and no custom authentication providers
- TLS: TLS 1.2 and above only
Most quotas can be increased through AWS Support, but the architectural limitations remain fixed.
Despite its many advantages, VPC Lattice isn't suitable for all use cases. Consider alternatives when your architecture includes:
- Streaming Services: Applications requiring persistent connections, like MCP (Model Context Protocol) servers that stream AI responses
- Real-time Applications: Chat applications, live dashboards, or collaborative tools
- Workaround: Possible but complex - requires deploying a WebSocket broker in front of VPC Lattice services
- Global Applications: Services that need to span multiple AWS regions
- Disaster Recovery: Cross-region failover scenarios requiring seamless networking
- Workaround: Deploy separate VPC Lattice service networks in each region with application-level routing
- UDP Traffic: Applications using UDP protocols
- Custom UDP Protocols: Proprietary communication protocols based on UDP
- Workaround: Use AWS PrivateLink or Transit Gateway for UDP communication patterns
- Large File Transfers: The 1MB response size limit makes large data transfers inefficient
- Workaround: Use direct S3 access or other data transfer services
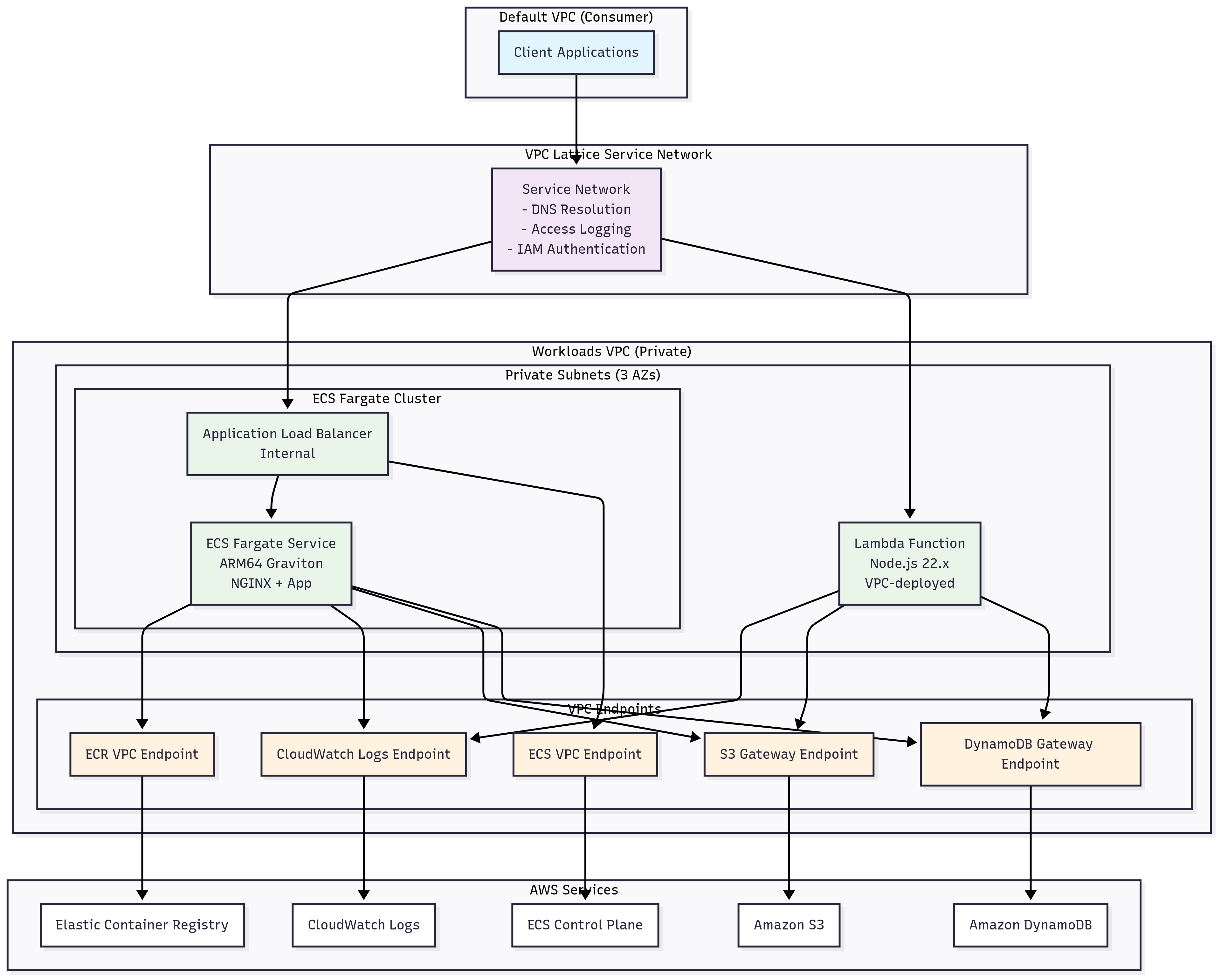
This repository contains a complete AWS CDK application that demonstrates how to deploy a fully functioning VPC Lattice stack. The demo includes both Lambda and Application Load Balancer (ALB) services connected through VPC Lattice.
The CDK application deploys:
- VPC Infrastructure
- VPC Lattice Service Network
- Lambda Service
- Container-based Service
- Network Isolation: Workloads run in private subnets with no internet access
- Service Mesh: VPC Lattice provides Layer 7 and Layer 4 routing with service discovery
- Multi-Compute: Shows both serverless (Lambda) and containerized (Fargate) services
- AWS Integration: VPC endpoints enable private access to AWS services
- Observability: Access logging and CloudWatch integration
- Security: IAM-based authentication and security group controls
- Client in Default VPC makes request to service through VPC Lattice
- VPC Lattice routes request based on service name and path
- For container service: Request → ALB → ECS Fargate task
- For Lambda service: Request directly to Lambda function
- Services can communicate with each other through VPC Lattice
- All AWS service calls go through private VPC endpoints
The CDK code demonstrates several best practices:
- Modular Design: Each component is implemented as a separate construct
- Security First: IAM policies follow least privilege principle
- Observability: Integrated logging and monitoring
- Infrastructure as Code: Complete deployment automation
To deploy this demonstration:
# Install dependencies
npm install
# Bootstrap CDK (if first time)
cdk bootstrap
# Deploy the stack
cdk deployAfter deployment, you can access both services through their VPC Lattice endpoints, demonstrating seamless service-to-service communication across different compute paradigms (serverless and container-based).
Estimating costs for service networking solutions requires understanding several pricing dimensions. Here's how VPC Lattice pricing compares to alternative approaches:
- Service Network Hourly Charge
- VPC Association Hourly Charge
- Data Processing Charges
- Request Charges
- Access Logging
- Consolidate Service Networks: Use fewer service networks with more services per network
- Minimize Cross-AZ Traffic: Deploy services in the same Availability Zones to reduce data transfer costs
- Monitor Data Processing: Track data volume to identify optimization opportunities
- Selective Logging: Configure logging only for critical services
- Pros: No hourly charges, only standard data transfer fees
- Cons: Requires more complex networking setup and management
- Best for: Simple point-to-point connectivity with low management overhead
- Hourly attachment fee: $0.05/hour per attachment
- Data processing: $0.02/GB
- Best for: Hub-and-spoke network architectures connecting many VPCs
- VPC endpoint fee: $0.01/hour per endpoint
- Data processing: $0.01/GB
- Protocol support: Any TCP traffic (Layer 4)
- Use case: Private access to AWS services or third-party SaaS
- Best for: Secure connectivity to external services without internet routing
- Higher base cost but includes advanced Layer 7 features
- Protocol support: HTTP/HTTPS and TCP
- Use case: Internal microservices communication with advanced routing
- Best for: Applications requiring Layer 7 routing, TCP connectivity, authentication, and observability
Application modernization should always look beyond the workload architecture. Ensuring sound networking is as important as the workload itself and VPC Lattice does simplify a lot of the decisions. Choose this option over peering or transit gateway for micro services architecture when Layer 7 capabilities are required and platform scalability is paramount. As always, when calculating total cost of ownership, consider not just the direct AWS charges but also the operational overhead, security benefits, and development efficiency that each solution provides.